SOC 2 is an audit procedure that displays your company’s commitment to providing trusted services.
All service providers should be trying to achieve SOC 2 Compliance and Certification. User Entities – i.e., companies that are using your service – want to know you’re proactively taking care of their needs.
The guide covers the factors required to achieve SOC 2 Compliance and Certification.

What is SOC 2?
SOC 2 is part of the AICPA’s Service Organization Controls standards based on the AICPA’s Trust Service Criteria. First published in 2011, it follows the same format as the SOC 1 Report. However, the AICPA’s Assurance Services Executive Committee listed a different set of criteria to be measured for SOC 2 Compliance.
The ‘SOC 2 Report on Controls at a Service Organization’ creates a baseline of information safety at a service provider. It is Proof of your organization’s compliance will come in the form of a SOC 2 Report. You can think of the User Entity’s needs as the risks they’re exposed to while they are using your service.
The 5 Trust Principles of SOC 2 Certification
The Trust Service Criteria are defined as principles. Each of the tenets covers an area relating to the safety and control of a user’s information. You should keep in mind that a control – such as a software module – could satisfy one or more of the required principles.
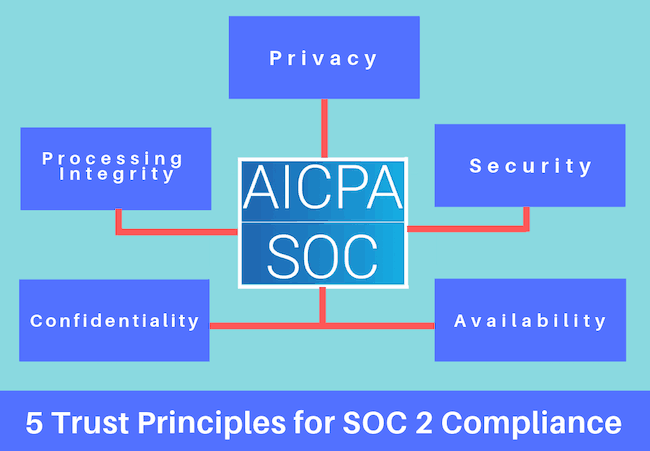
Security
The company should be able to show that their system is protected from unauthorized access. They should also prevent unauthorized disclosure and limit any damage that could influence the availability, integrity, confidentiality, and privacy of the information.
Availability
The system should have controls in place to ensure it’s available as needed by the User Entity.
Processing Integrity
Data and information processing should be checked whether they are complete, valid, accurate, timeously executed and authorized.
Confidentiality
Information that is designated as confidential should be protected according to the User Entity’s needs.
Privacy
The organization should address the User Entity’s needs when they collect, use, retain, disclose and dispose of Personal Information.
Establishing a SOC 2 Compliance Framework
The company’s risk assessment determines the framework for SOC 2 Compliance. The risks are based on the type of services provided.
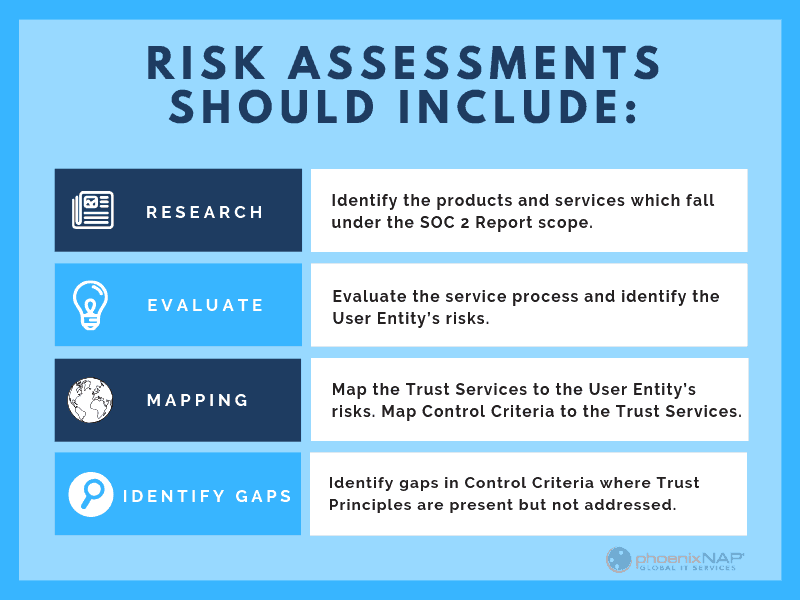
The risk assessment should include the following six steps:
1. Identify the products and services which falls under the SOC 2 Report scope.
2. Evaluate the service process and identify the User Entity’s risks.
3. Map the Trust Services to the User Entity’s risks.
4. Map the Control Criteria to the Trust Services.
5. Identify gaps in the Control Criteria where Trust Principles are present but not addressed.
6. Map internal user controls to the gaps.
The Scope of SOC 2 Reports
Unlike strict PCI Requirements, it is not required for service providers to cover all 5 Trust Principles in a SOC 2 report. Only those that relate to their activities should be included in the scope. Care should be taken when deciding on which of the TSPs will be in the report.
For services that are outsourced, the supplier will have to show adequate controls are in place at their company’s site as part of your report.
Business Processes for the Trust Principle Assessment
The four main areas that are covered during the assessment of the company’s TSP Controls are:
Business Policies
Written policies that are relevant to the Trust Principles.
Communicating the System
The company has disclosed its policies to stakeholders and the responsible entities. This includes the users of the system.
Control Procedures
The company has procedures that will achieve the principles set out in the policies.
System Monitoring:
The company monitors the system and takes action to ensure compliance with the policies.
SOC 1 vs. SOC 2 Reports
Two types of SOC reports can be prepared. The type of report your company will need will likely depend on your User Entity’s needs. A SOC 1 Report deals with the controls at financial institutions while service-orientated companies prepare a SOC 2 Report.
Type 1 Report
The Type 1 Report records the state of the system at a point in time. This will include a description of the system, a written assertion by management, the designed controls, and the Service Auditor’s expressed opinion.
Type 2 Report
A Type 2 report further records the operating effectiveness of the system over a period of time. In addition to the items listed in Type 1, the Type 2 Report will also contain the test results of the system’s controls. It uses the 5 Trust Principles to assess the company’s risk and how they are managing exposure.
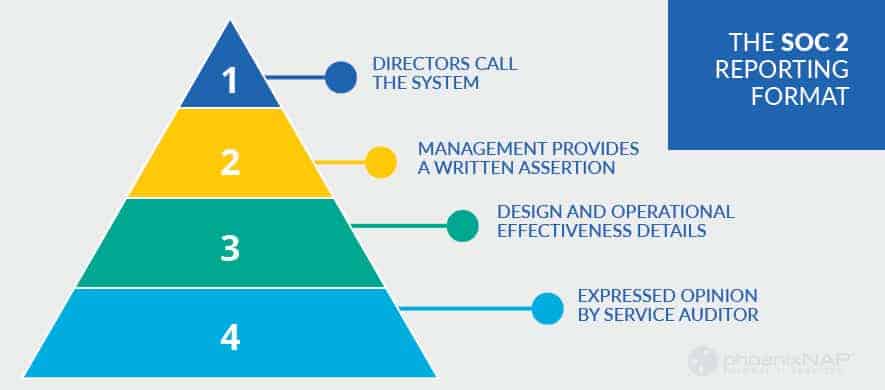
The SOC 2 Reporting Format
The Report has four main sections. Each section covers aspects of the system design, implementation, including whether it is complete and adequate.
Directors Call the System
The description of the system covers details about the services the company offers. It lists the infrastructure (such as hardware and software) that the data processing is done by. Boundaries that relate to these tasks should be recorded.
Additional items to keep in mind as part of the system description:
- Audit compliance solutions
- Risk assessment processes
- Varied system configurations at different locations
- Incident identification and response planning
The system description identifies the Trust Service Principles that should be covered. This enables you to map your Control Criteria to them and measure how effective your system is.
Management Provides a Written Assertion
This section contains the assertions made by management regarding the controls they’ve chosen to use. This is an opportunity to explain each of your methods and the controls that serve the Trust Services Criteria.
If the privacy principle forms part of the report, proof of compliance with the commitments stated in the privacy practice must be shown.
If a subservice is used for any portion of your system, this section should include:
- Details on how information is provided or received from the service provider.
- Controls at the service provider that deals with the handling, processing, maintenance, and storage of information.
Trust Principles that are excluded from the report should be listed along with the reasons why they are not covered.
Design and Operational Effectiveness Details
Section 3 of the SOC 2 Report contains a list of the controls that were designed.
If you are preparing a Type 1 Report, list the designed controls that meet the TSP criteria. For a Type 2 Report, you should include the test results for each of the designed controls. This can be in done in a table format.
To create a suitable control design, your company has to identify the risks that stand in the way of achieving your TSP. You will have to see if your control works as described and make sure there are no other risks that stop you from reaching your TSP.
Expressed Opinion by Service Auditor
The Auditor’s opinion will be based on:
- Whether the description of the system was fair.
- If the controls work as they are supposed to (for a Type 2 Report this is done over a period of time).
- If the description presents how the system was designed and built.
- It doesn’t leave out or distorts information regarding the system.
- The company complies with its privacy practices (if it was part of the scope).
As part of their opinion, the Service Auditor will list deviations and areas that lack control in the system.
Remember – SOC 2 Certification Creates Trust
When you achieve SOC 2 Compliance and Certification, it will inspire and grow trust in your organization.
User Entities may ask for a SOC 2 Report, and they will specify their TSP needs in the request. In cases like this, the report should be based on their request.
Each Trust Principle covered in the SOC 2 Compliance Report is an opportunity to earn the trust of your clients.



